In this post, we will learn the steps to configure SSTP VPN on Windows Server 2019 using a Self-signed certificate.
Secure Socket Tunneling Protocol (SSTP):
Secure Socket Tunneling Protocol (SSTP) is a tunneling protocol developed by Microsoft. SSTP uses a TCP connection (port 443) for tunnel management.
SSTP provides a mechanism to encapsulate PPP traffic over the SSL channel of the HTTPS protocol. The use of PPP allows support for strong authentication methods such as EAP-TLS. SSL or TLS provides transport-level security with enhanced key negotiation, encryption, and integrity checking.
Note: You should use a certificate from public CA in the production environment. As we are just testing the SSTP configuration, so we will use a self-signed certificate in this guide.
Understanding the SSTP Test Lab:
- WS2K19-DC01: Domain Controller and DNS.
- WS2K19-VPN01: Member Server.
- WS10-CLI01: Windows 10 Client Machine.
Step:1 Install Remote Access Server role on Windows Server 2019:
1. The first step is the installation of the Remote Access Server role. Open Server Manager Console and start role and feature installation wizard. Select the Remote Access Server role.
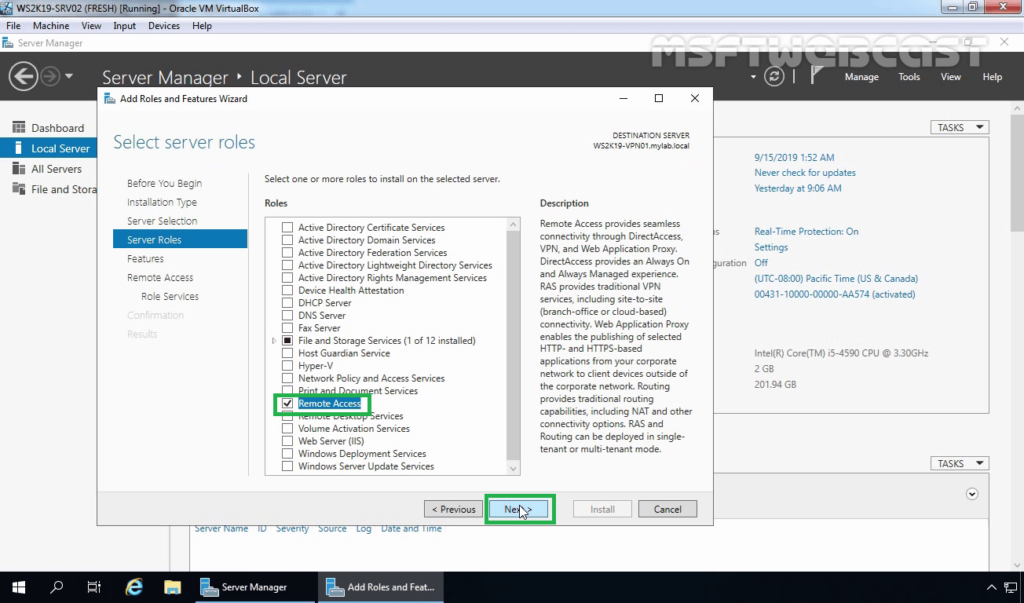
2. On select role services, select DirectAccess and VPN (RAS) role service. Click Next and finish the installation.
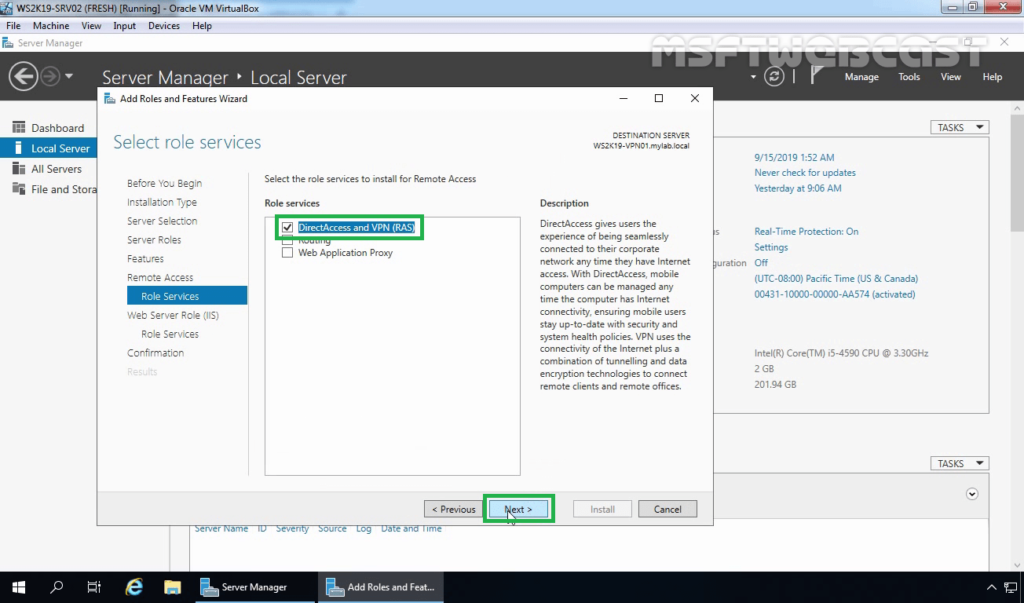
3. When the installation finished, click on Open the Getting Started Wizard. Leave the console open, and move to the next step to create a self-signed certificate.
Step:2 Create a Self-signed Certificate using the IIS manager.
4. On the member server, open the Server Manager console. Click on Tools and select Internet Information Services (IIS) Manager.
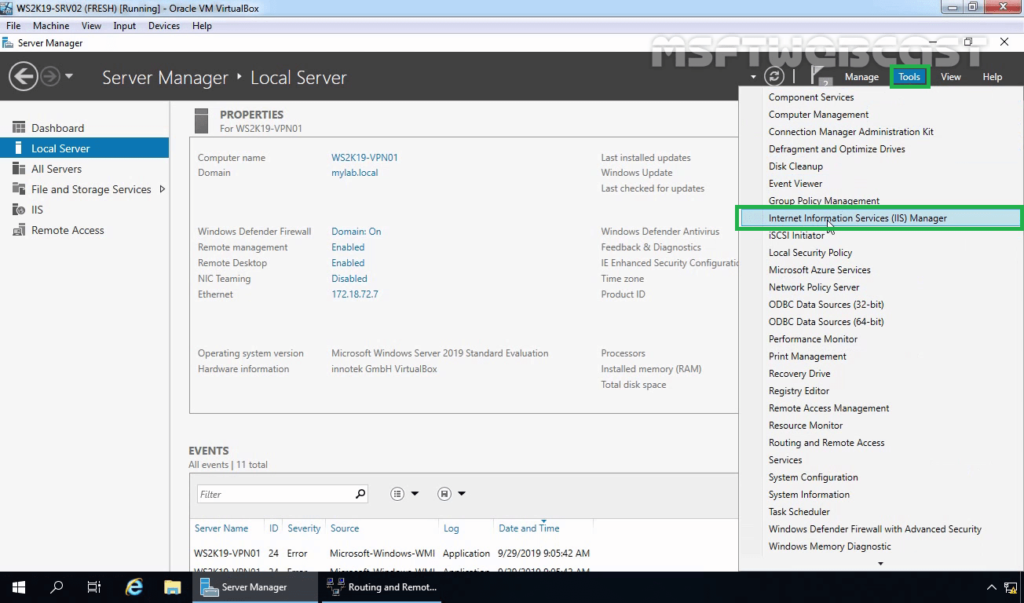
5. Click on the server name (WS2K19-VPN01) in the connections column on the left and double-click on Server Certificates.
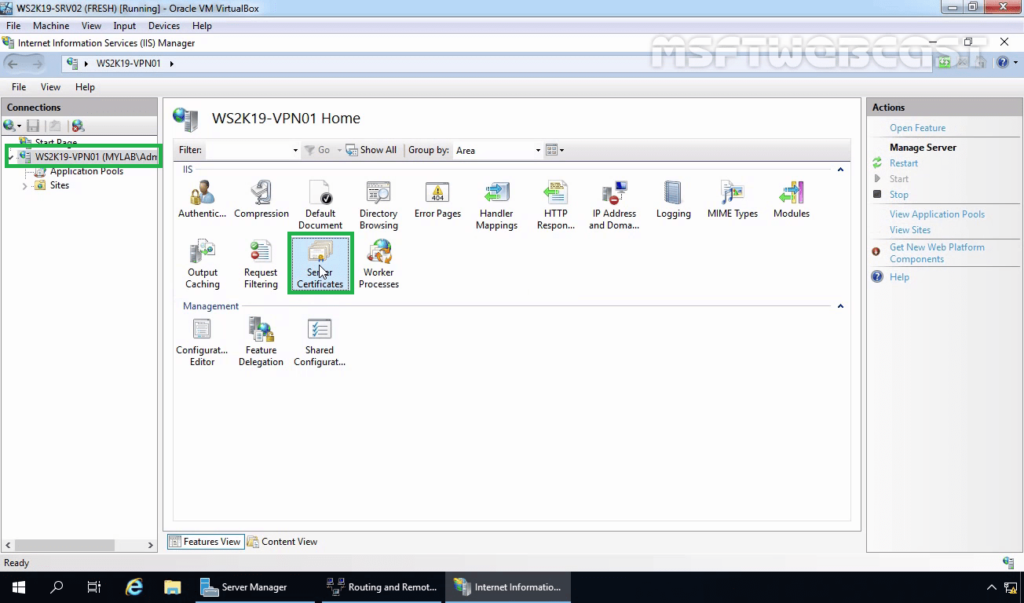
6. Click on Create Self-Signed Certificate in the Actions column on the right.
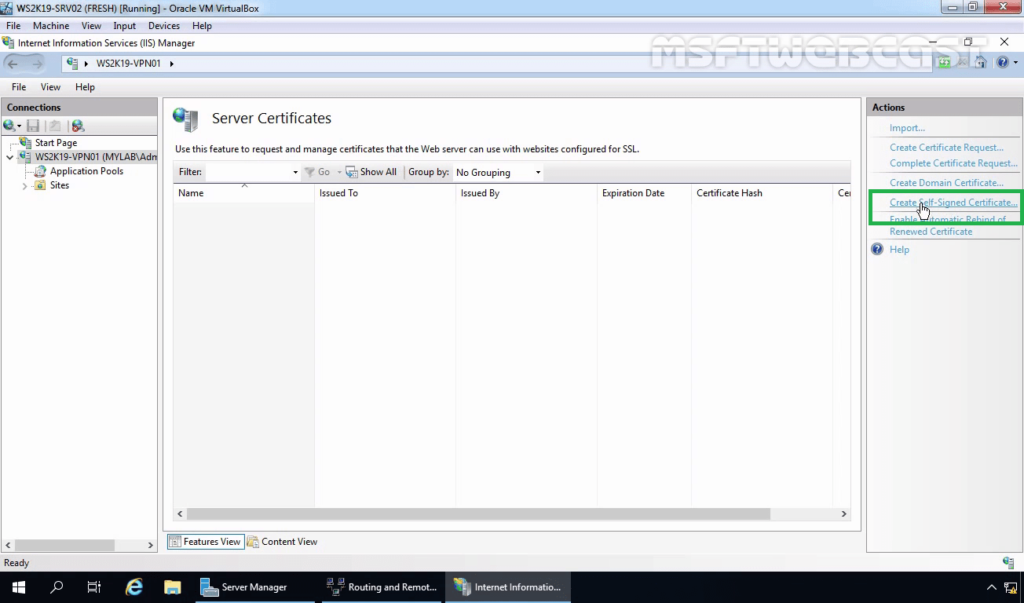
7. Enter the friendly name you wish to use to identify the self-signed certificate, and then click OK to complete the process.
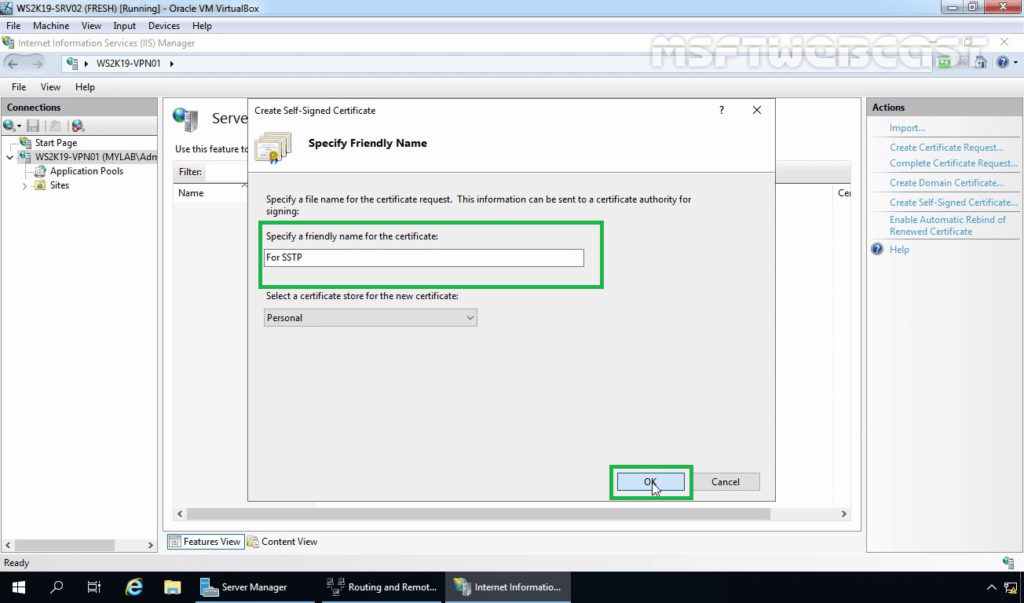
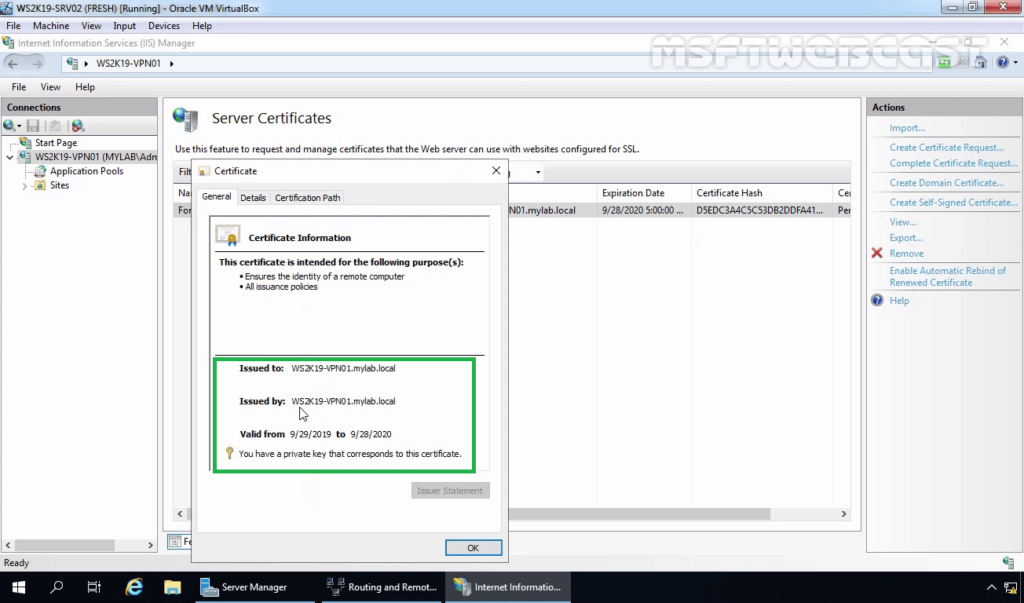
8. You now have an IIS Self Signed Certificate listed under Server Certificates. Double-click on Certificate. The validity of the Self Signed Certificate is one year.
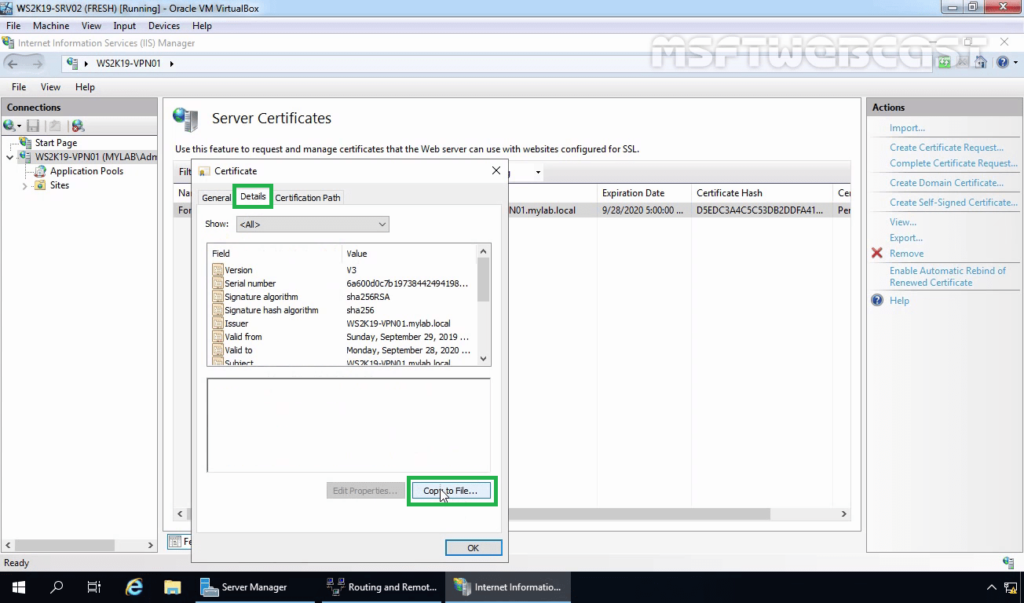
Step:3 Export a self-signed certificate:
9. Click on the Details tab. Click on Copy to File.
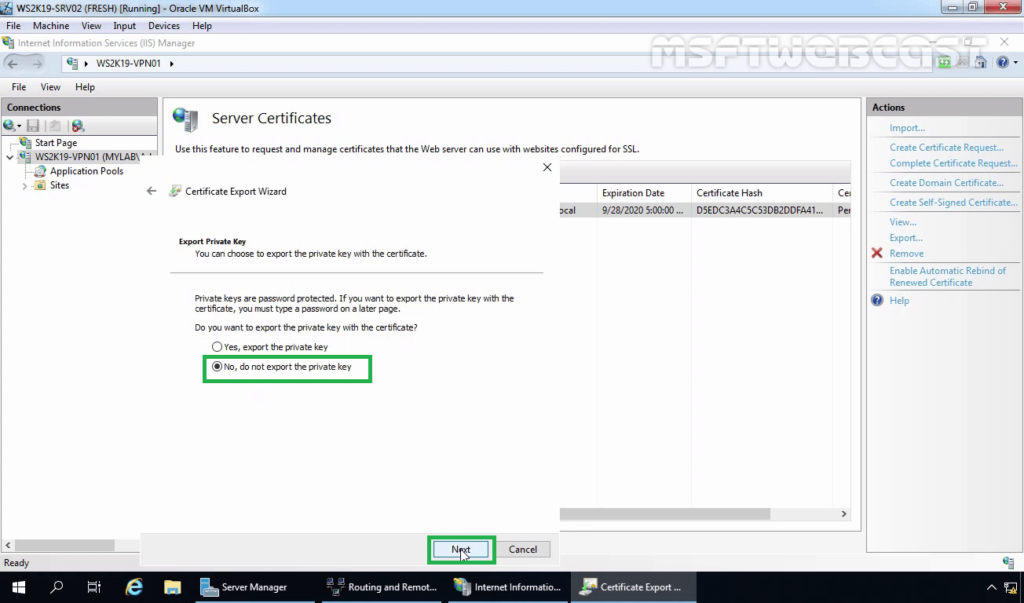
10. Select No, do not export the private key. Click Next.
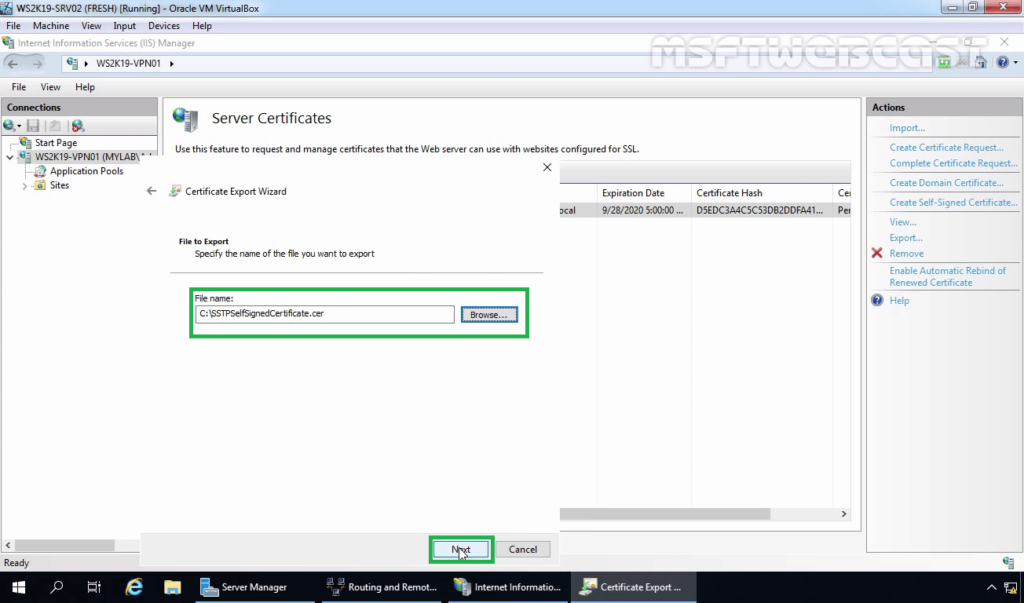
11. Specify the location to save the file. Click Next.
12. Click on Finish. Click on OK on the confirmation message console.
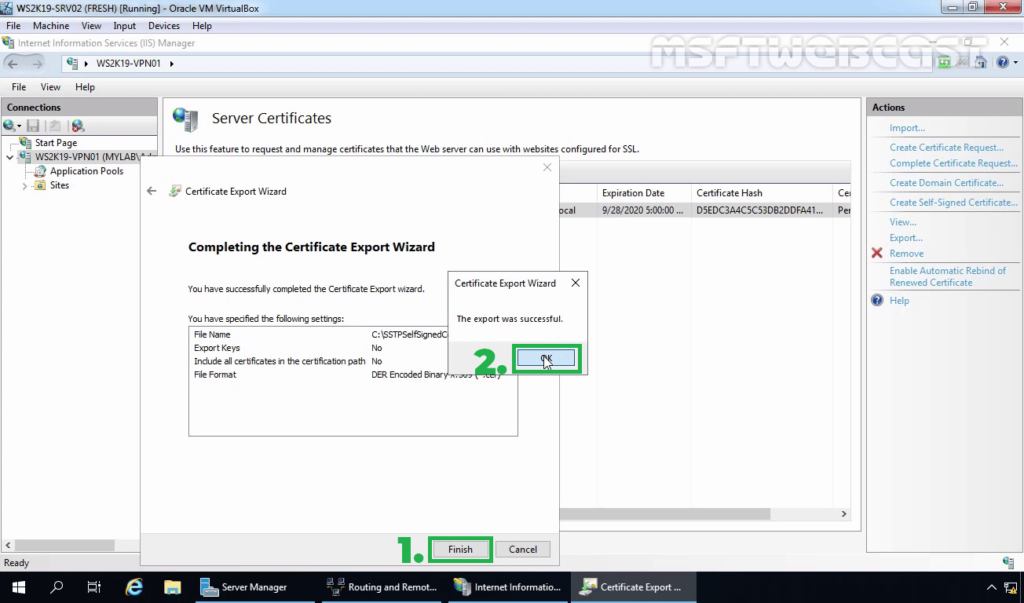
Note: You need to copy this .cer certificate file to Windows 10 machine. The simple way to do this is by sending this .cer file using an email.
Step:4 Configuring Remote Access Service and SSTP VPN:
13. On configure Remote Access page, click on Deploy VPN only.
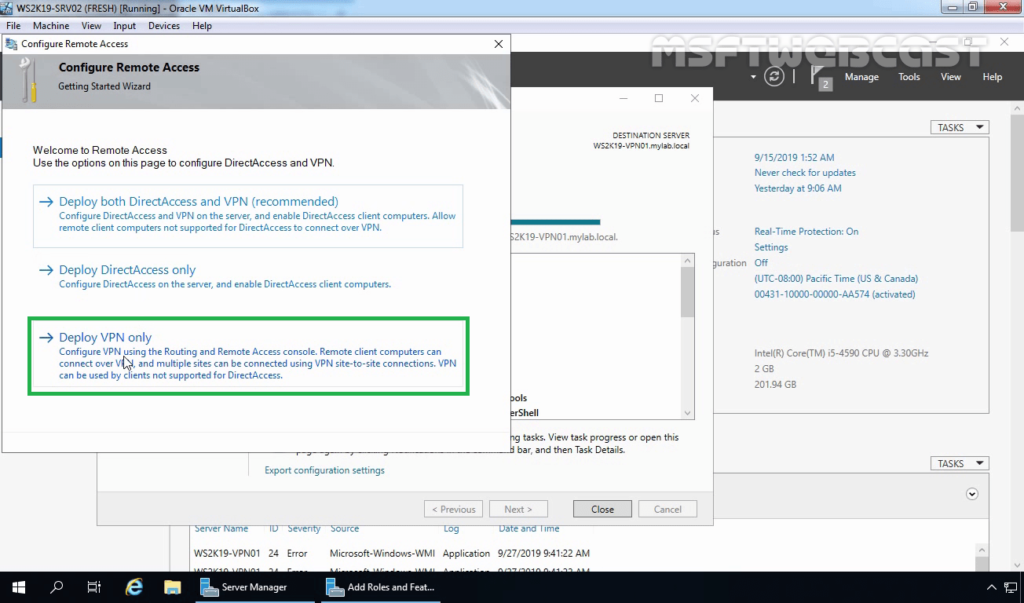
14. That will open the Routing and Remote Access Management Console. You can also open the management console from the Tools menu.
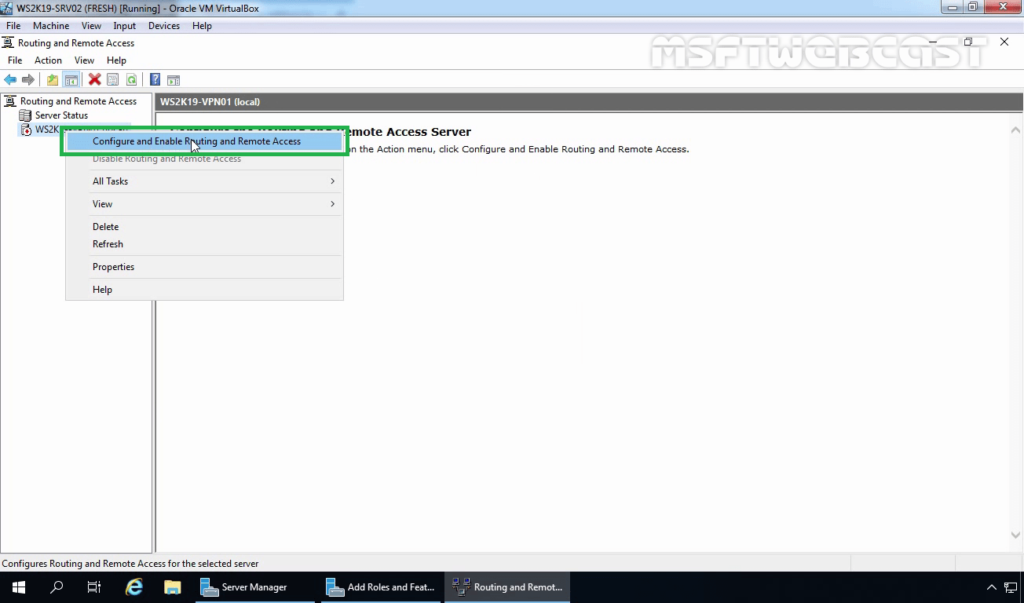
15. Right-click on the Server name and select Configure and Enable Routing and Remote Access.
16. On Welcome screen, click Next.
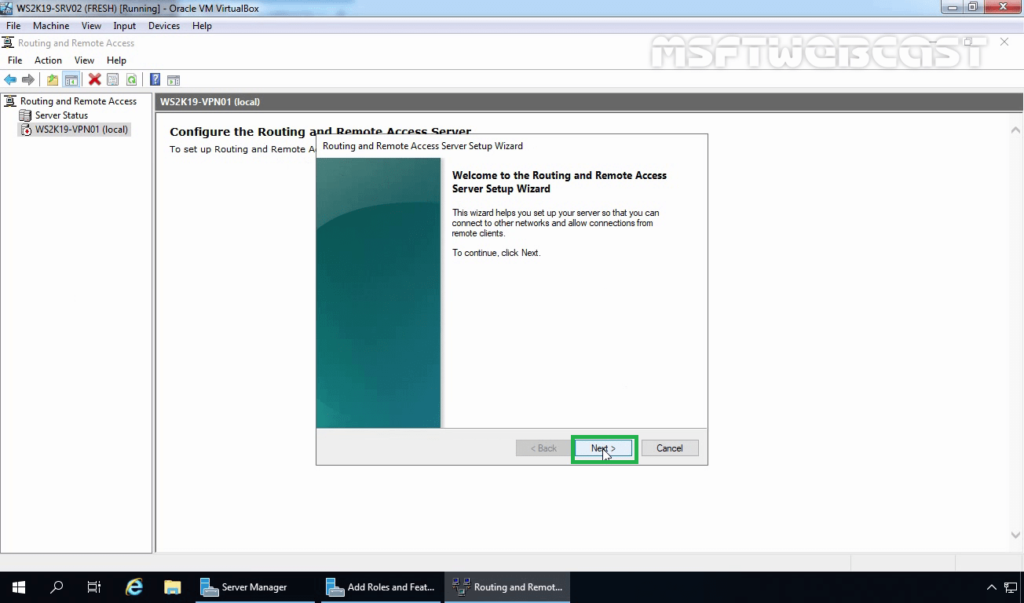
17. On the Configuration page, select the Custom configuration radio button. Click Next.
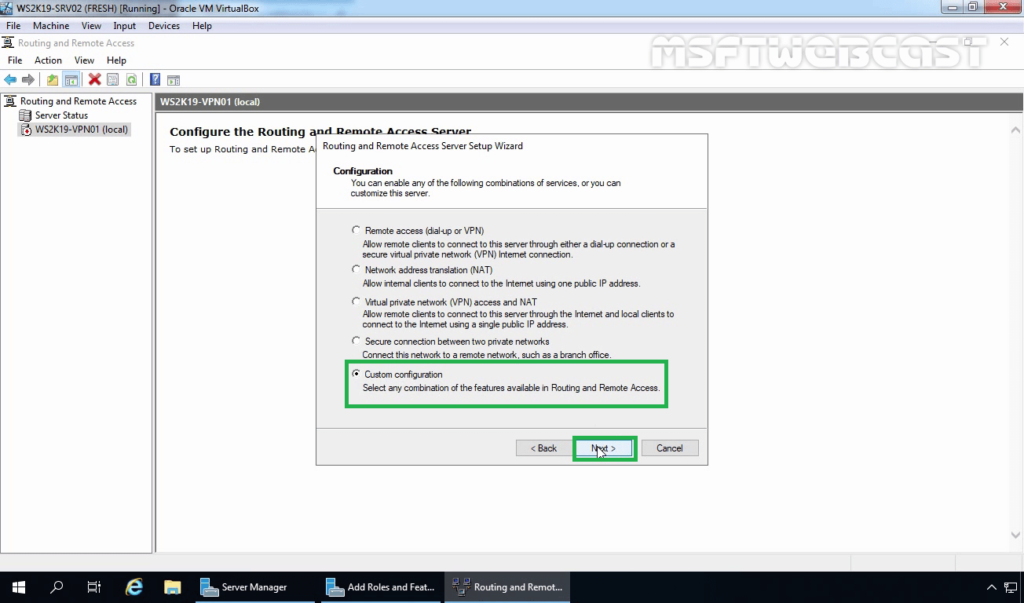
18. On select the service page, select VPN Access. Click Next.
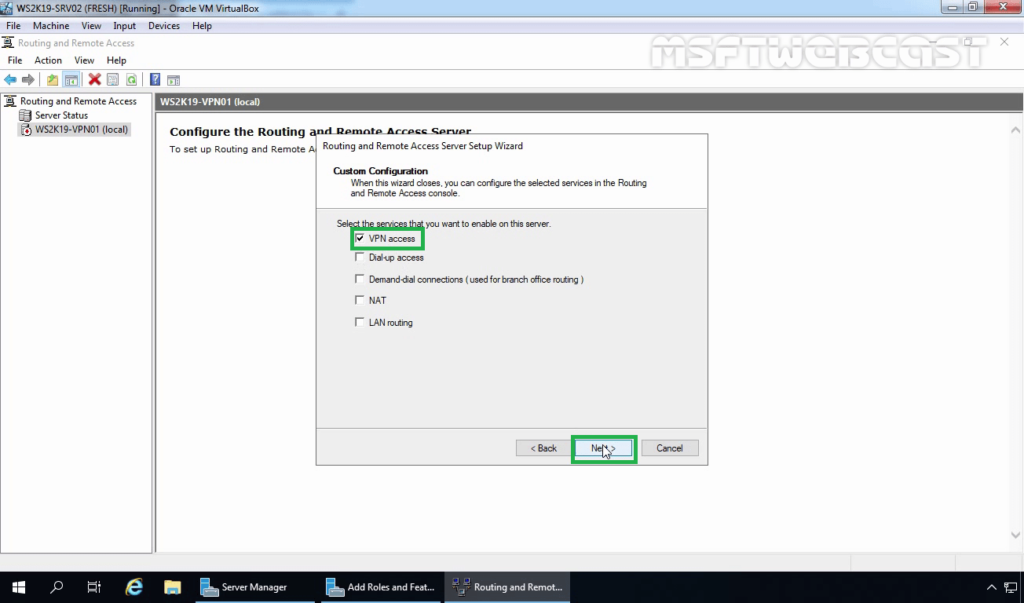
19. After clicking on the Finish, it will ask you to start the service. Click on Start service.
20. Now you will see a green up arrow beside your server name.
Step:5 Configure SSTP settings and specify the IP Address range:
To configure SSTP VPN, we need to set up specific settings in the VPN server’s properties section.
21. Right-click on the server name and click on Properties.
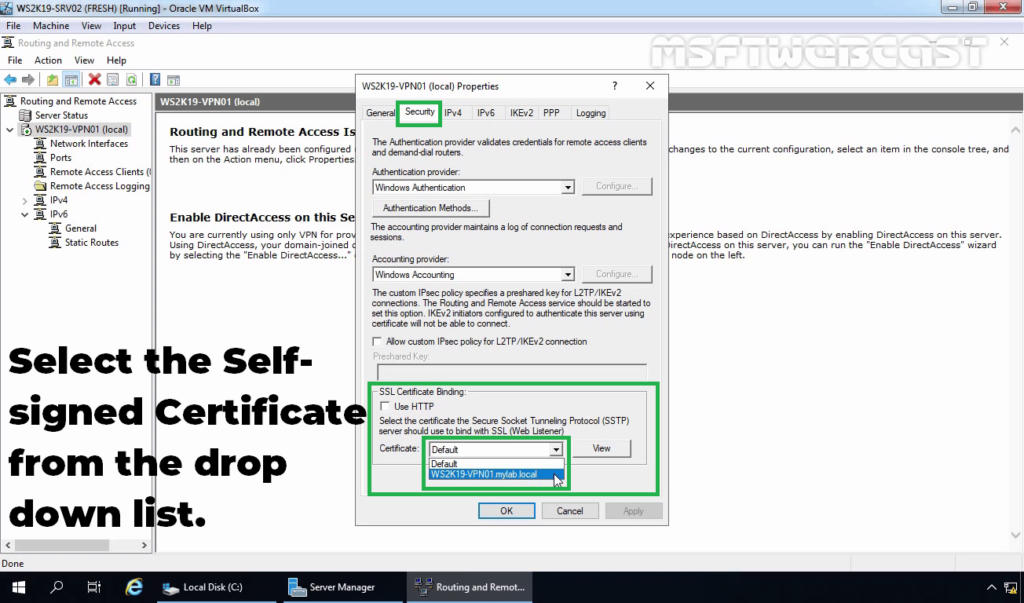
22. Click on the Security tab. Under SSL Certificate Binding, select the self-signed certificate that you just created earlier.
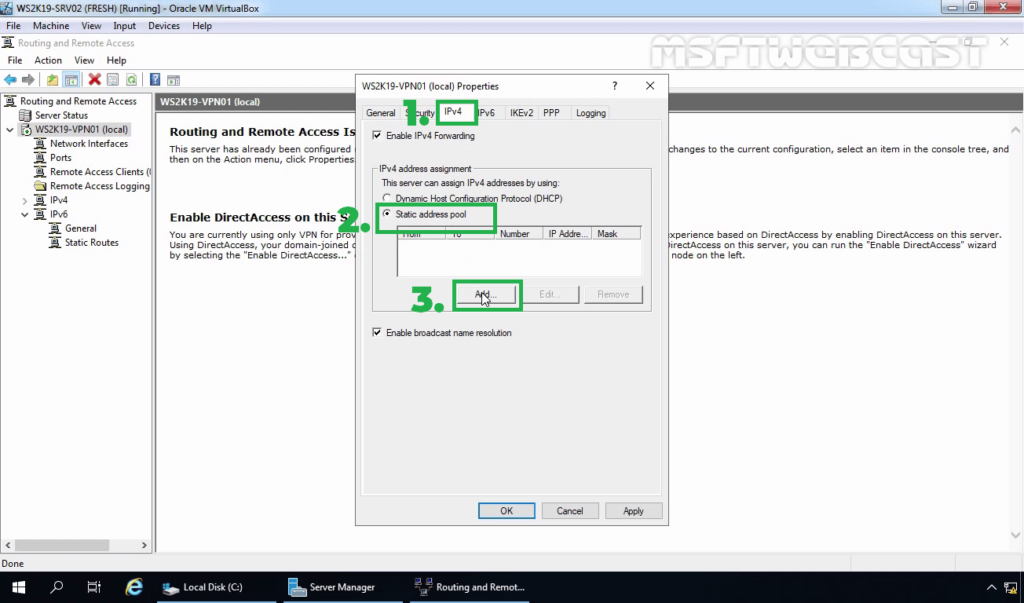
23. Click on IPv4 Tab. Select the Static Address Pool radio button.
24. Click on Add and specify the IP address range. Click on OK.
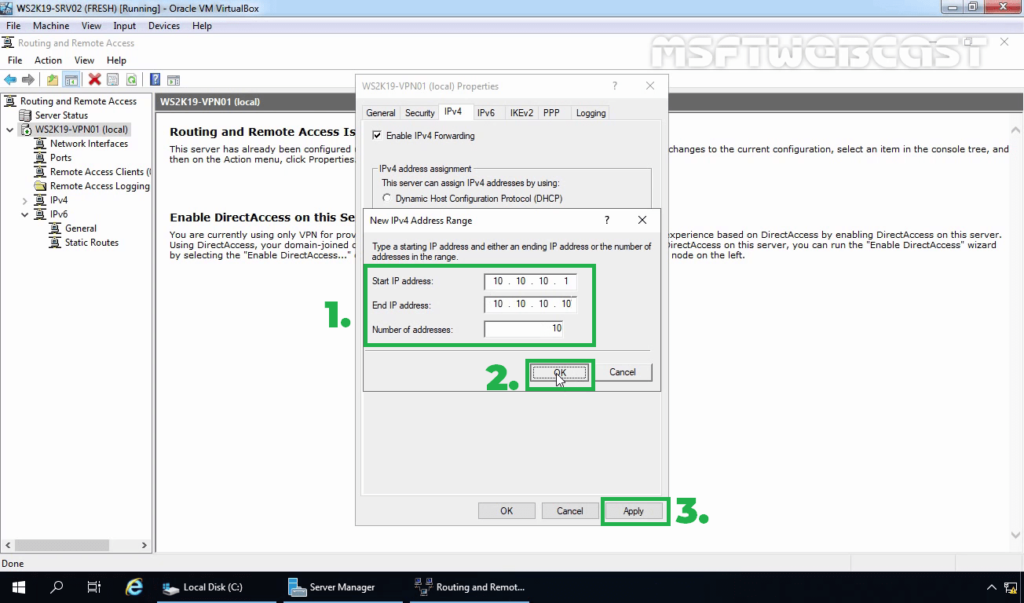
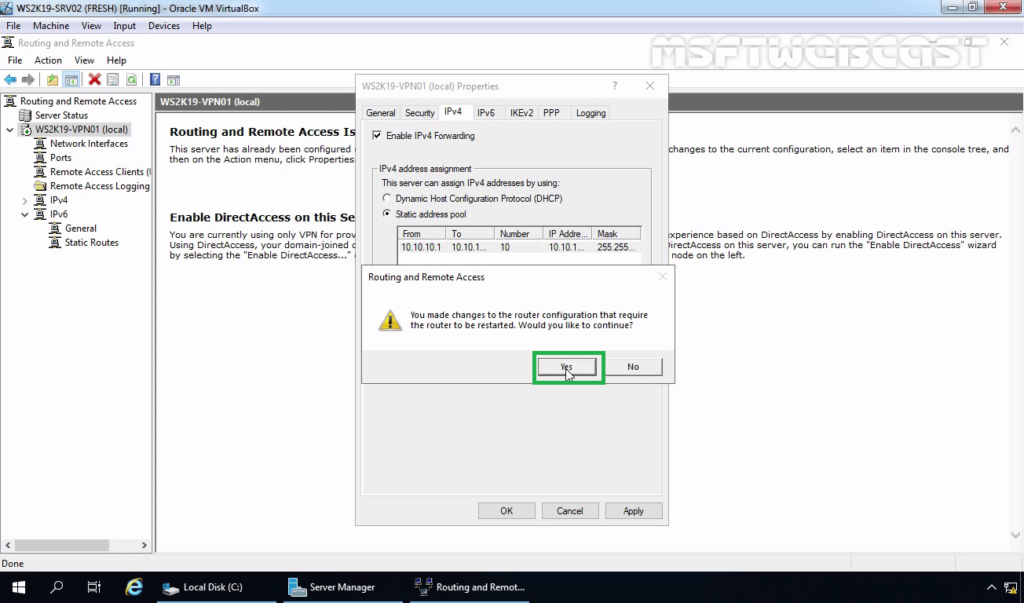
25. Click on Apply to save the changes to the VPN server. It will ask to restart the Routing and Remote Access service. Click on yes to do so.
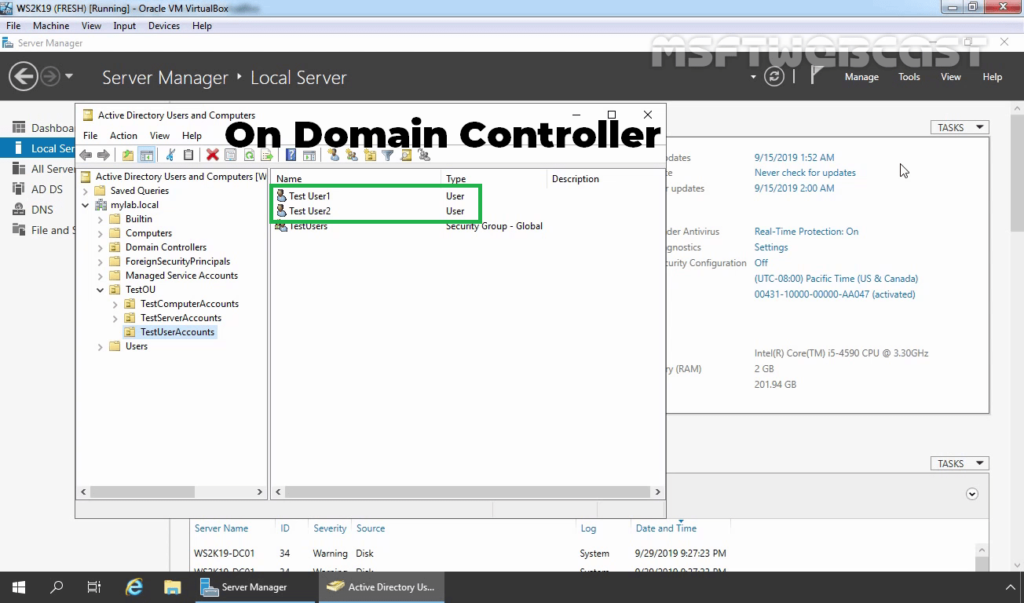
Step:6 Create AD User and allow dial-in access:
26. On Domain Controller, Open Active Directory Users and Computers snap-ins. Create AD users name Test User1 and Test User2.
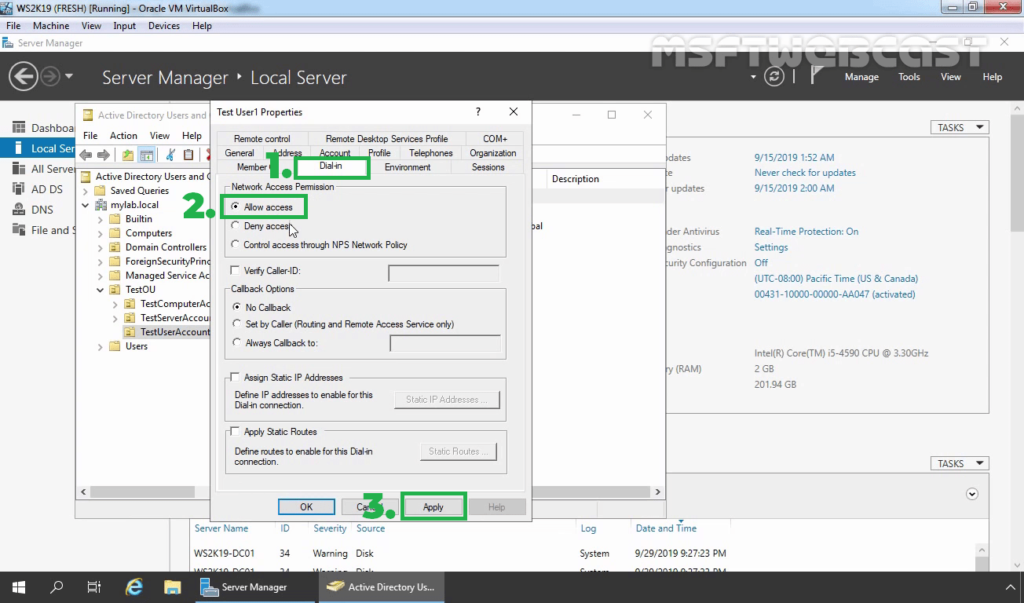
27. Enable dial-in access for selected VPN users by opening the user properties and selecting Allow access on the tab Dial-in.
Note: If you want, you can configure Network Policy Server to allow VPN users to connect to the VPN server running on Windows Server 2019.
Step:7 Import a self-signed certificate on Windows 10 machine:
Once you get a .cer certificate file, you need to import the certificate on the local computer. You need to store the certificate under the Trusted Root Certification Authorities store.
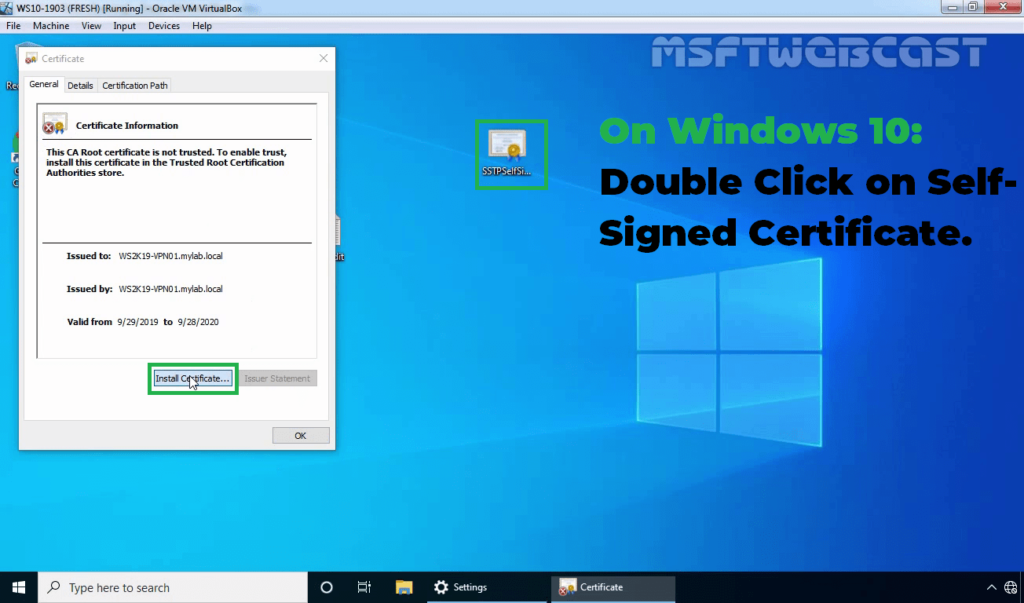
28. Double-click on SSTPselfsigned.cer file. Click on the Install certificate.
29. Select Local Machine and click Next.
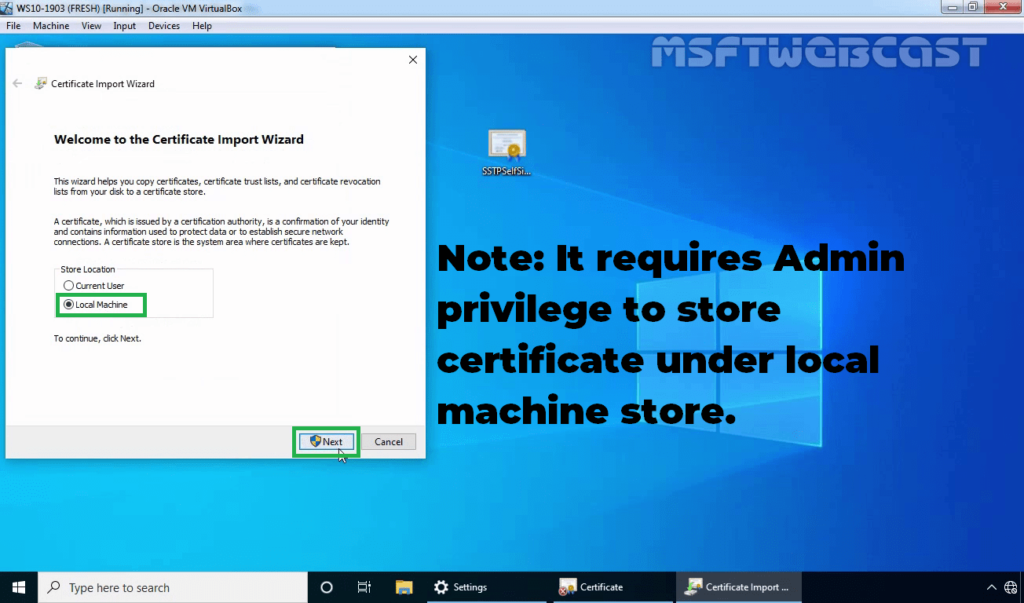
30. Select Place certificates in the following store radio button and click on Browse.
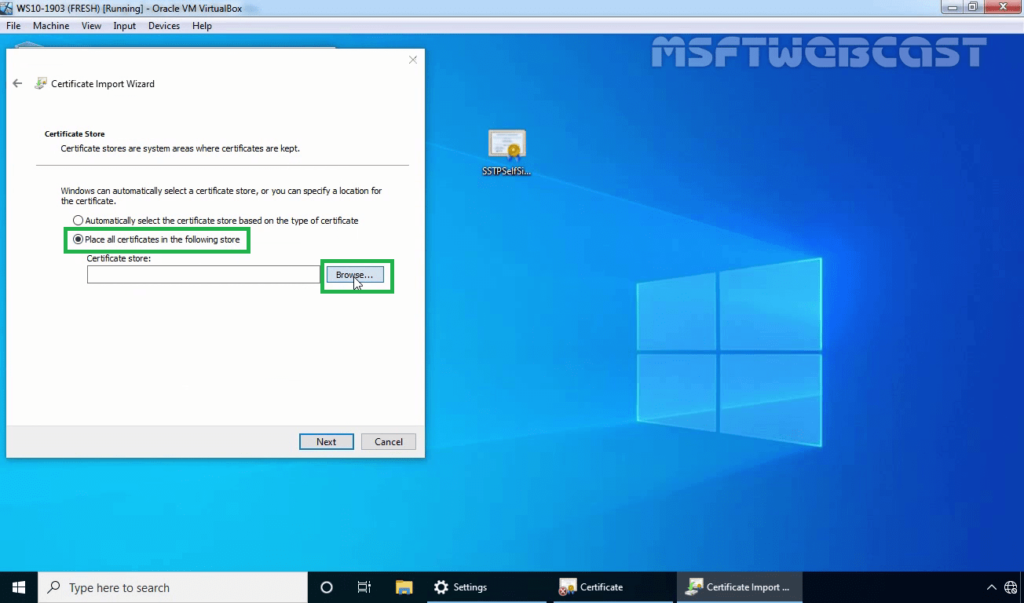
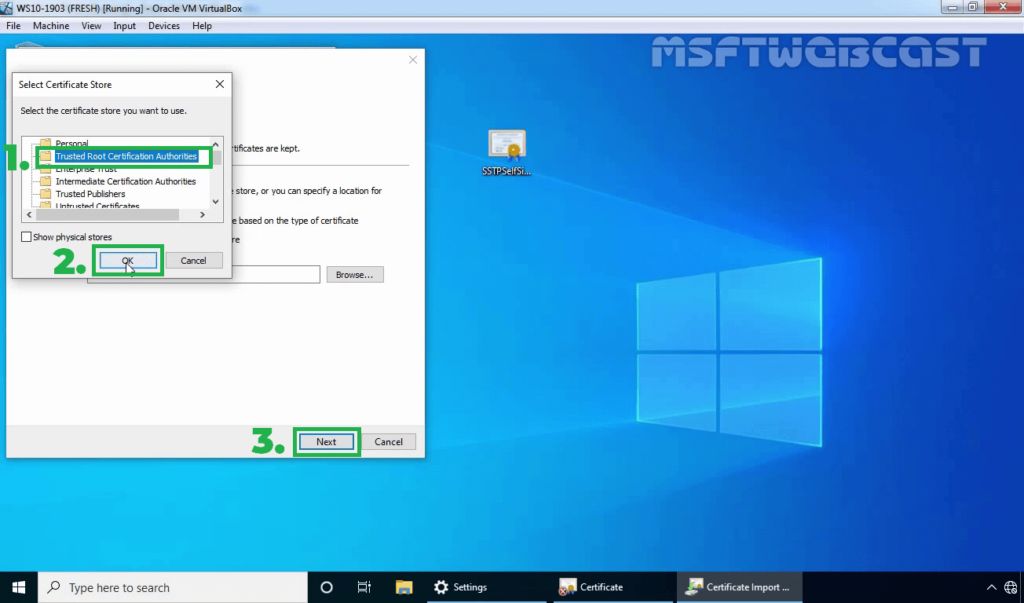
31. Select the Trusted Root Certification Authorities store and click OK. Click Next.
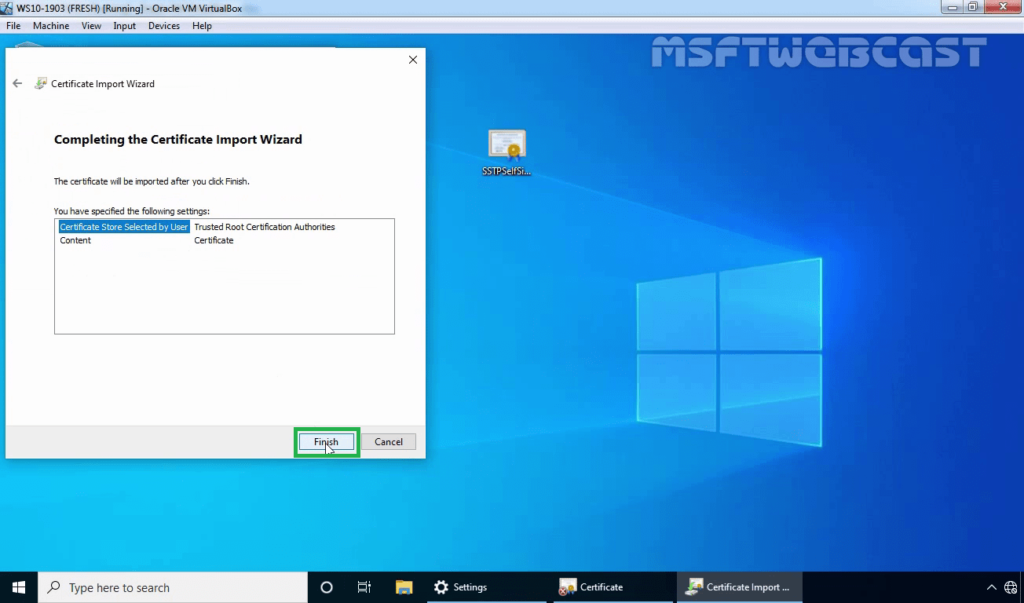
32. Click on Finish to complete the import process.
Step:8 Test SSTP VPN configuration:
On Windows 10 client machine, we need to create a new VPN connection.
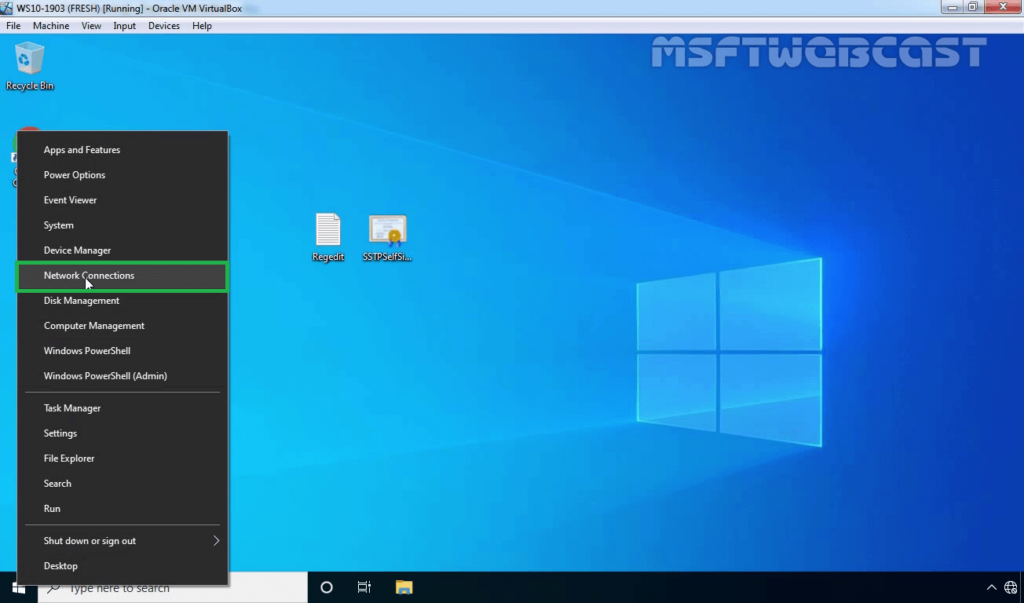
33. Right-click on the Start button and select Network Connections.
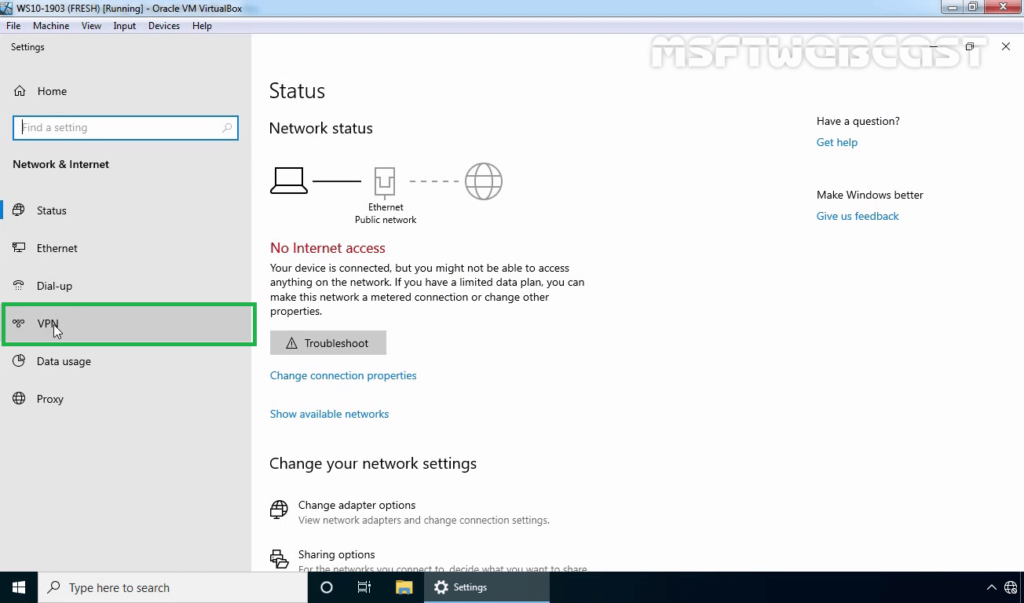
34. On left-pane, click on VPN.
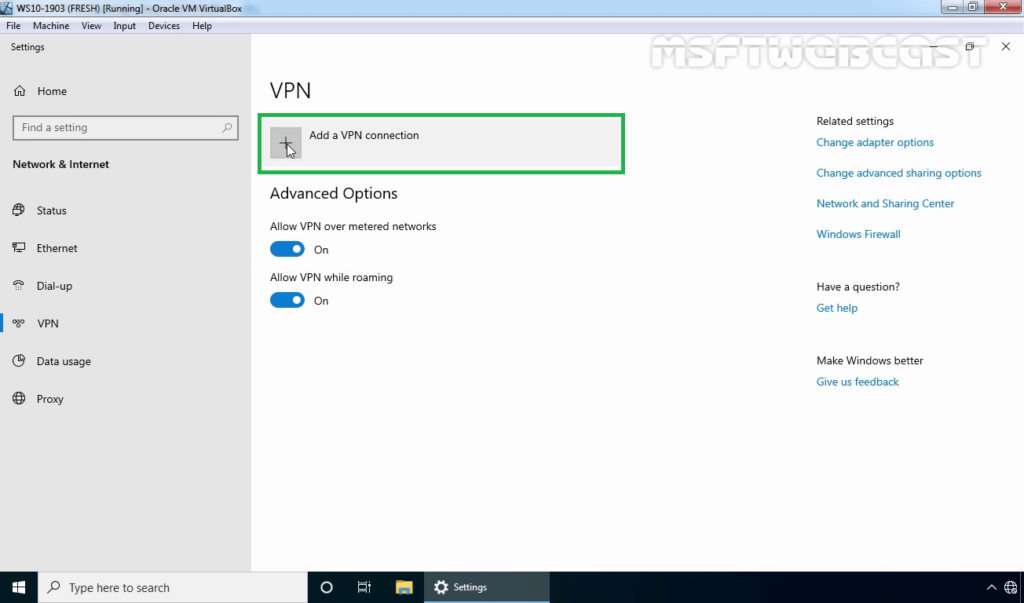
35. Click on add a new VPN connection.
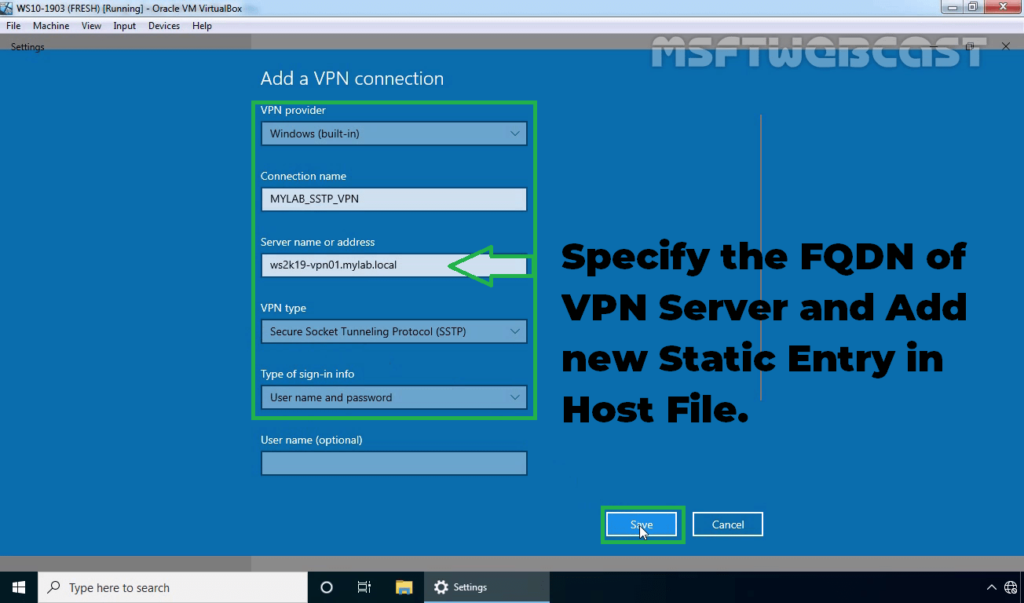
36. Specify the required information for the VPN connection.
- VPN Provider: Windows (Built-in)
- Connection Name: Name of your choice
- Server Name or IP Address: FQDN of VPN server
- VPN Type: SSTP (Secure Socket Tunneling Protocol)
Click on Save.
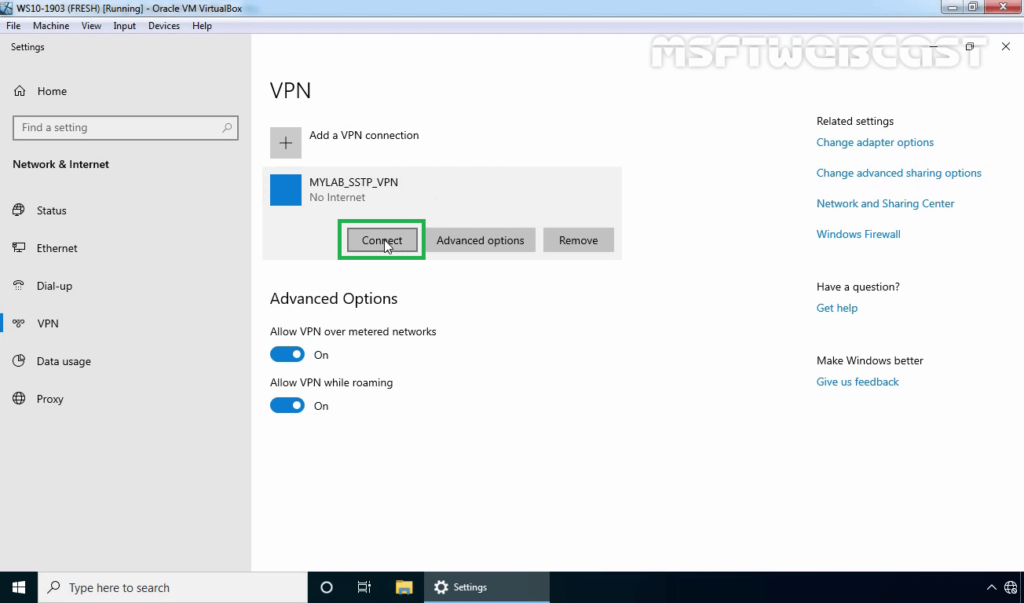
37. Select VPN connection and click on Connect.
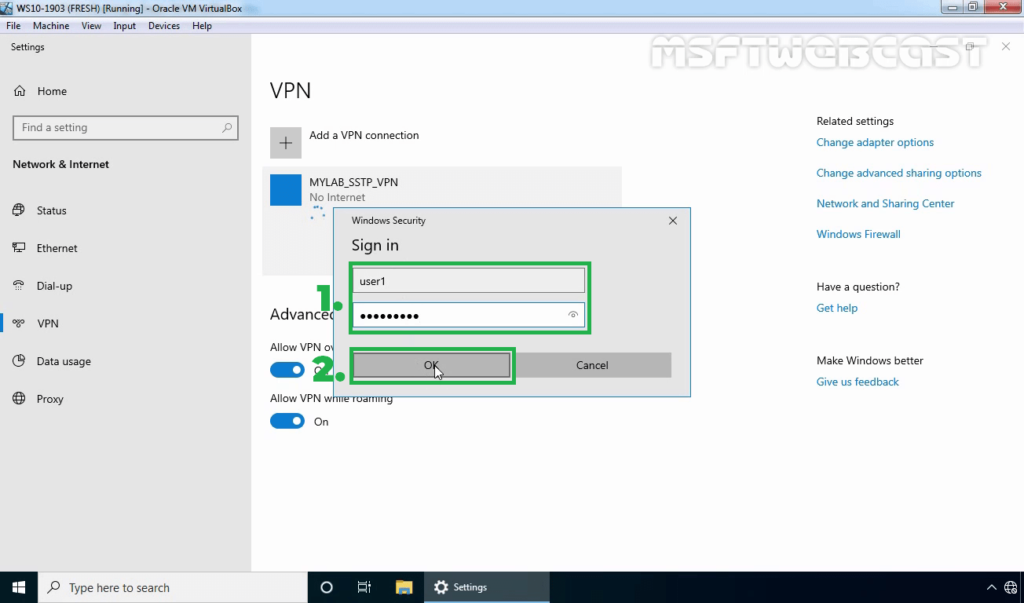
38. Specify a username and password to connect the VPN server. Click OK to connect.
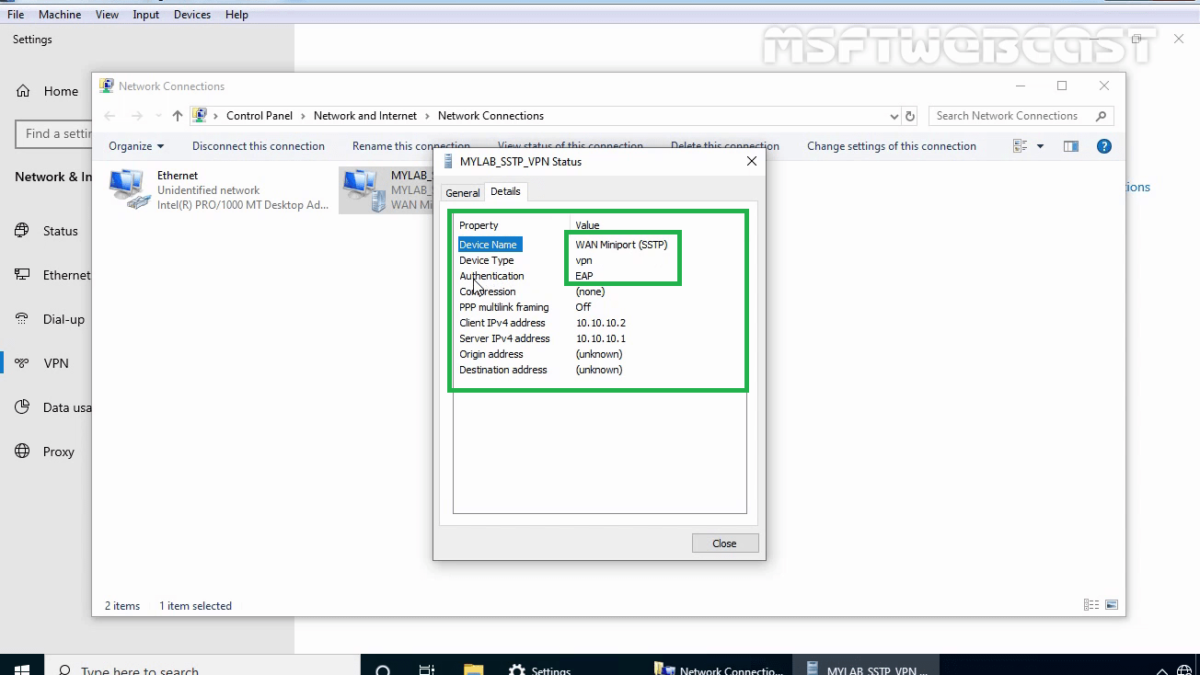
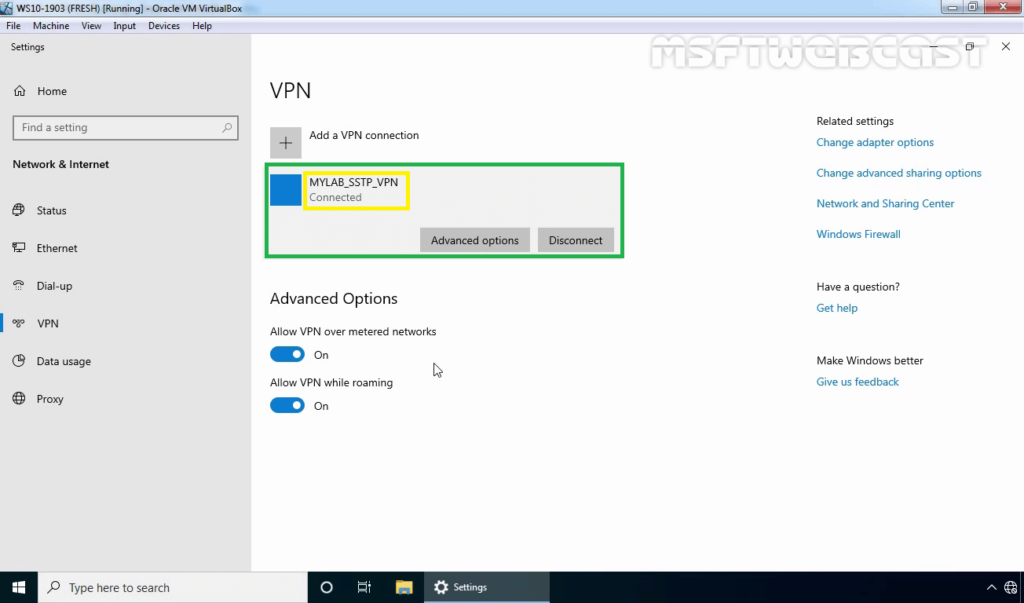
39. Verify the VPN connection is successfully connected with the VPN server using SSTP protocol.
On Windows 10 Client Machine:
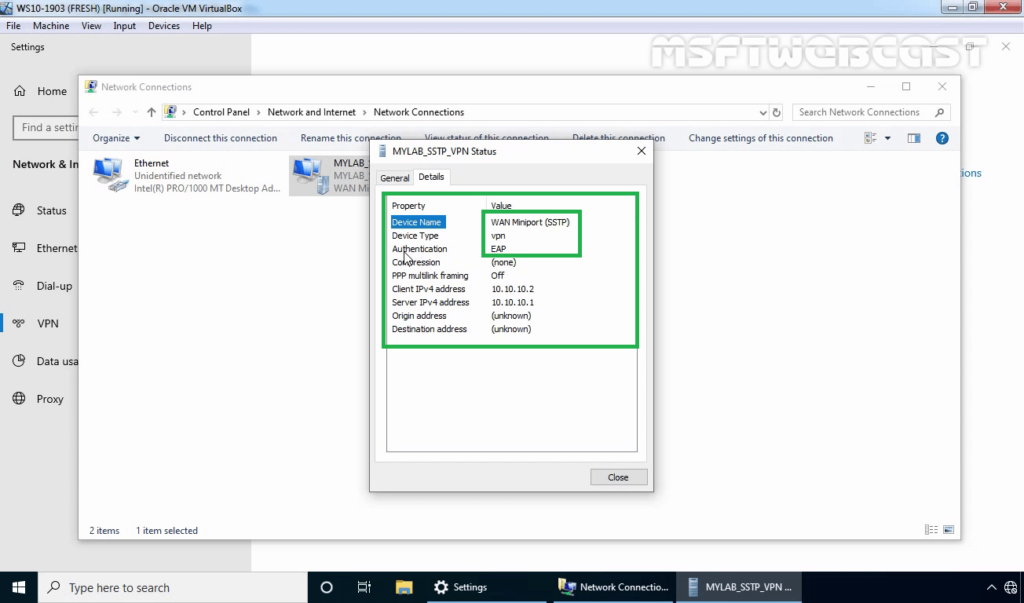
40. Press Windows Key and R key together. At Run menu type ncpa.cpl and press enter to open Network Connection console.
41. Right-click on VPN connection and click on the Status button.
42. Click on details to see information about VPN connection like Authentication Method etc.
In this article, we have seen the steps to Install and Configure SSTP VPN using Self-signed Certificate on Windows Server 2019 and Windows 10.
Thank you for reading.
Related Articles:
- PART-1 How to Install Remote Access Service on Windows Server 2019
- PART-2 How to Install and Configure VPN in Windows Server 2019
- PART-3 Configure Network Policy Server (NPS) for VPN in Windows Server 2019
- PART-4 Configure Port Forwarding and Test VPN Connection on Windows 10