In this post, we will see the steps for creating fine-grained password policies on Windows Server 2019 Active Directory Domain Environment.
Fine-grained password policies allow you to specify multiple password policies within a single domain so that you can apply different restrictions for password and account lockout policies to different sets of users in a domain.
For this post, I have created two users and one security group in Active Directory. Both users are members of that security group. Once we create a Fine-grained password policy, we would be applying it to a group named HRUsers.
Users: HR User1 and HR User2.
Group: HRUsers.
To create FGPP, login to the Windows server 2019 domain controller using a domain admin account and click on Server Manager.
To create a new Fine-Grained Password Policy, We need to open the Active Directory Administrative Center (ADAC).
On server manager console, click on Tools and select the Active Directory Administrative Center.
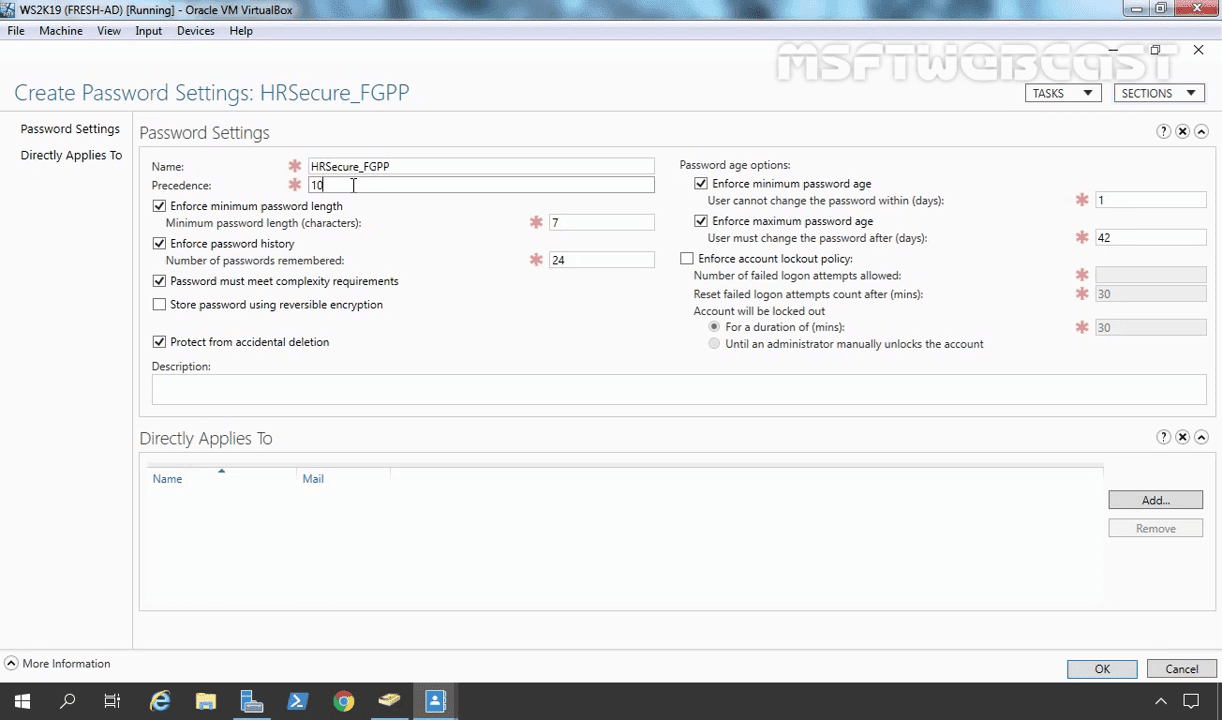
It will open the following Create Password Settings screen.
In the Name text box, type the name of the Password Settings Container (Ex. HRSecure_FGPP).
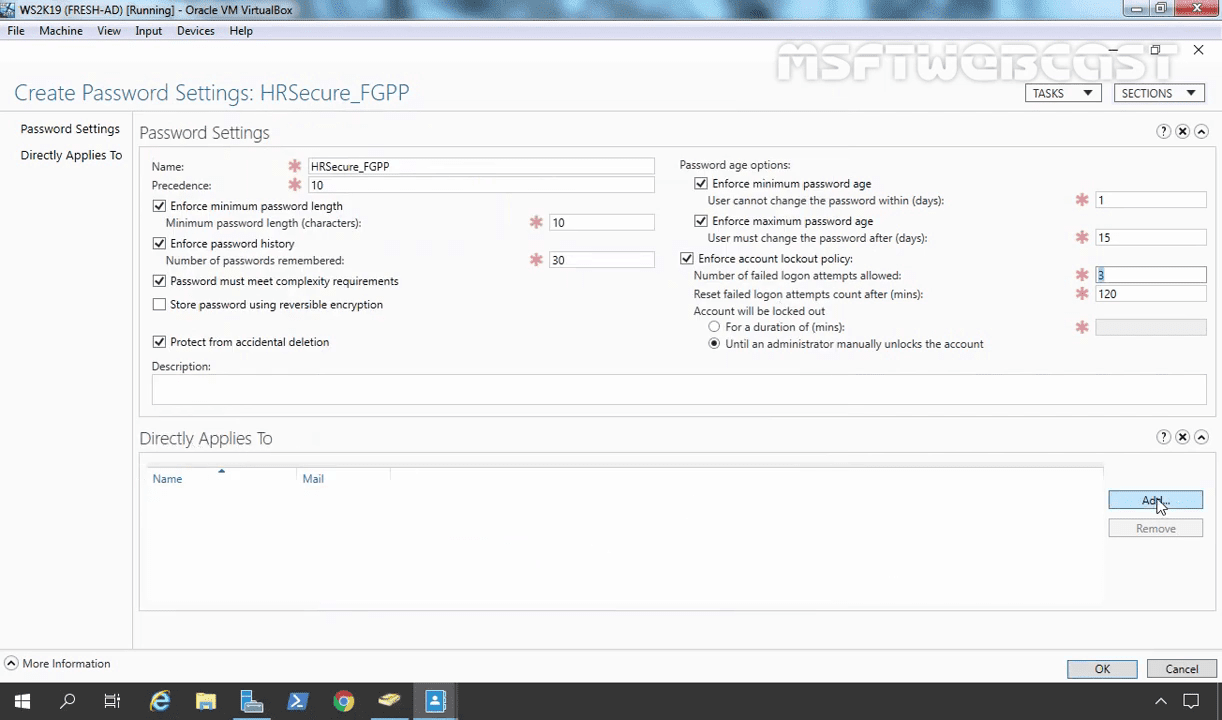
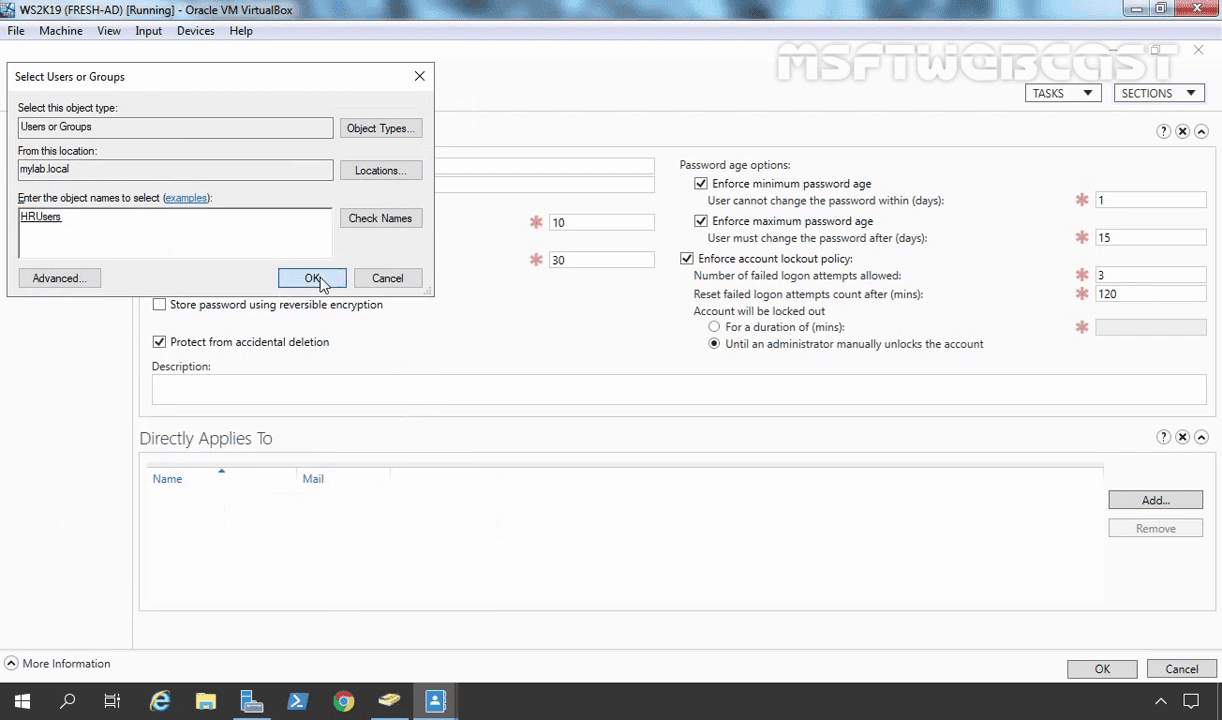
Now you need to apply this PSO (Password Settings Object) to a group called HRUsers.
(Note: A Password Settings Object (PSO) is an Active Directory object. This object contains all the settings that you can find in the Default Domain Policy GPO.)
Click on Add
Done! We have successfully applied the Fine-Grained Password Policy on members of HRUsers group but still we want to verify that.
To view the resultant PSO.
Locate the security group HRUsers. Right-click on the security group and select properties.
Here we can verify that HRSecure_FGPP PSO is applied to our security group.
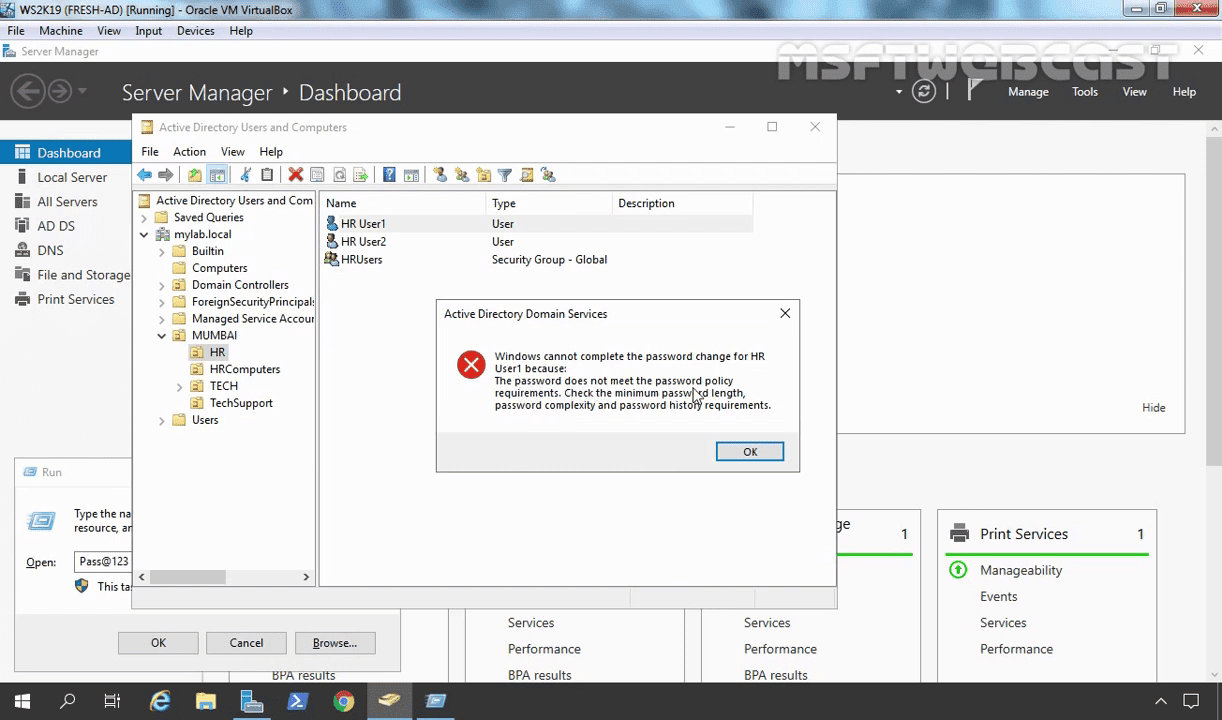
Even as an administrator if we try to setup a simple password.